One of the most popular online security and optimization tools today is open proxy, also known as open proxy. So What is an open proxy?? Are open proxies really safe and effective? Let's find the answer with Hidemyacc in the following article.
1. What is an open proxy?
Open Proxy is a proxy server that acts as a bridge between a client (a user's computer) and another server (a website or online service). Anyone on the Internet can connect to open proxies to forward their online traffic through that proxy without authentication or authorization.

Open proxies forward requests and responses between clients and servers, allowing Internet users to access online content indirectly. They help hide your IP address from the websites and online services you access through them, thereby enhancing your online privacy. In contrast, a reverse proxy server receives requests from the client on behalf of the server and forwards them to the appropriate backend server.
2. Characteristics of Open Proxy
Open proxy is a type of server can be used for many different purposes, bringing significant benefits to users. Here are some outstanding features of open proxies:
-
Surf the web anonymously: Open proxies are often used to browse the web anonymously, preventing users from having their online activities tracked.
-
Bypass internet filters: They are used to access websites blocked in certain countries or regions, helping users bypass content restrictions.
-
Download and send large data: Open proxies can help avoid detection when downloading large files or sending large amounts of data, protecting privacy in the process.
- Hide IP address: Open proxy servers have the ability to mask users' IP addresses, allowing access to websites and services without being tracked.

3. Types of Open Proxy servers
Open proxy servers come in many different types, each serving specific purposes and applications. Here are the popular types of open proxy servers:
-
HTTP Proxy: Using the HTTP (Hypertext Transfer Protocol), this proxy server forwards HTTP requests from the client to the server. They are often used to access websites blocked in certain countries or regions, as well as to improve performance or surf anonymously.
-
SOCKS Proxy: SOCKS (Socket Secure) proxy server forwards network traffic from clients to servers. Like HTTP Proxy, SOCKS Proxy can help users bypass IP address restrictions, improve performance or security during web surfing.
-
SSL Proxy: SSL (Secure Sockets Layer) proxy servers forward secure traffic from clients to servers. They help protect data transmission and can be used to access blocked websites and improve performance or anonymity in web surfing.
-
NAT Proxy: A NAT (Network Address Translation) proxy server forwards traffic from a private network to a public network. They are commonly used to bypass IP address restrictions and improve network performance, while also supporting anonymous web surfing.
-
Reverse Proxy: A reverse proxy server acts as a gateway between the Internet and web servers. This system receives requests from the Internet, forwards them to origin servers, and provides functions such as access control, caching and load balancing.
-
Anonymous Proxy: This type of proxy hides the user's original IP address and provides an alternative IP address to the service provider.
-
Transparent Proxy: The transparent proxy server forwards the user's origin IP address to the service provider and can provide caching features.
-
Distorting Proxy: A shapeshifting proxy server changes a user's IP address to make it appear they are connecting from another location.
- Elite Proxy: This type of proxy not only hides the user's original IP address, but also provides an alternate IP address and changes the User-Agent header, which makes it appear that the user is connecting from another device .
4. Advantages and disadvantages of Open Proxy browser
Open proxies have outstanding features in both advantages and disadvantages, depending on usage and user needs. To understand better What is an open proxy? Let's look at the main benefits and limitations of this type of proxy:
4.1. Advantage
-
Low cost: Open proxy servers are often free, helping users save on access costs. This is especially useful for those on a limited budget.
-
Accessibility: Open proxies allow users to access restricted content, bypass geo-restrictions, or attack other networks with denial of service (DDoS) attacks. They help users access websites and services faster than closed proxies.
-
Advanced security: Open proxies can provide an additional layer of protection between users and the Internet, helping to prevent malicious attacks. By routing traffic through an anonymous proxy, users can hide their IP address and location, making it harder for hackers to track.
-
Anonymous: Open proxies help hide users' IP addresses and locations, making it harder for websites and services to track user activity. This is especially beneficial for people who care about their privacy and security.
- Better access control: Open proxy allows better access control compared to other proxy servers. Administrators can set up different access policies for each user, control who can use certain resources, and ensure that only authorized users can access. They are also capable of blocking unwanted requests and filtering bad traffic, providing a higher level of network and application security.

4.2. Disadvantages
-
Security risks: Anyone can access open proxies, making them open to abuse to hide identities and carry out attacks such as DDoS, malware, and hacking.
-
Resource abuse: Open proxies can be used to access restricted content, bypass geo-restrictions, or perform denial-of-service attacks against other networks. This can lead to resource abuse, slowdowns, or even server crashes.
-
Privacy: Open proxies can be used to intercept and monitor user data and traffic, which may violate user privacy.
-
Legal issues: Open proxies can be used to access restricted content or bypass geo-restrictions, which can cause legal problems if they violate copyright laws or other regulations.
- Limited accessibility: Open proxies are not always available and may be blocked by firewalls, making them unreliable for some operations. They can also be slow and overloaded, making them less useful for activities that require quick access.

5. Some questions about open proxies
When working with open proxies, users may encounter some problems related to how their IP address is detected or banned. Here are common questions about open proxies and how to solve them:
5.1. Why is your IP address flagged as an open proxy?
Your IP address may be flagged as an open proxy for a number of reasons:
-
Server misconfiguration: If you use a proxy server on your network that is incorrectly configured and allows unauthorized access, Internet service providers (ISPs), web services, online platforms, and software Security software may flag your IP address as an open proxy.
-
Infected with malware or belonging to a botnet: If your server device or network is infected with malware or is part of a botnet, the system can act as an open proxy. Cyber criminals may have infiltrated your device and used it for malicious activities.
-
Used before: If the IP address you are using has been involved in abusive online activities, they may also be flagged.
-
Shared IP address: Sites may flag your IP as an open proxy if you are on a public network, like public Wifi, and share the address with other users used to proxy traffic.
-
Suspicious traffic patterns: If your IP address generates a large amount of traffic that has characteristics of an open proxy (for example, a high number of connection requests), proxy detection tools may flag it.
5.2. How to detect open proxies?
Organizations use many methods to detect open proxies. Here are some popular methods:
-
Port scanning: A tool or service that automatically scans a range of IP addresses to find open ports associated with open proxies.
-
Analyze traffic behavior: Some systems monitor network traffic patterns and look for high traffic volumes, large numbers of connection requests, and unusual patterns of proxy behavior.
-
Analyze DNS queries: DNS requests for domains related to proxy services or anonymizers may generate warnings.
-
Monitor access logs and anomalies: Access logs of web servers and network devices may show unusual traffic patterns, such as a single IP making too many requests.
-
Block list: Organizations maintain lists of open proxies and malicious IP addresses. Network administrators and security tools check these lists when flagging IPs with proxy-like behavior.
-
Report from the community: Users and network administrators report suspicious IPs and proxy-like behavior to organizations, helping detect open proxies.
5.3. How to determine if your IP is an open proxy?
To maintain your online reputation and ensure your network security, check and verify if your IP address is an open proxy. Here are instructions to do this:
-
Use an online proxy checker: Many online proxy checkers can verify if your IP address is flagged as an open proxy.
-
Check the public IP reputation list: Find public IP reputation lists or block lists maintained by cybersecurity organizations and ISPs and check your address.
-
Analyze your network traffic patterns: Review your network traffic patterns for unusual behavior such as high connection request volume and proxy-like activities.
-
Check server and proxy configuration: Make sure that your server and proxy configuration are not incorrectly set up to act as an open proxy.
-
Contact your Internet service provider: If you believe your IP address has been flagged incorrectly, request assistance from your Internet service provider to remove your address from the blacklist.
6. Instructions on how to turn off open proxies
When you understand clearly What is an open proxy?, the user will know that vDisabling open proxies on the network can help avoid security risks. Here are step-by-step instructions to turn off proxy on Chrome browser:
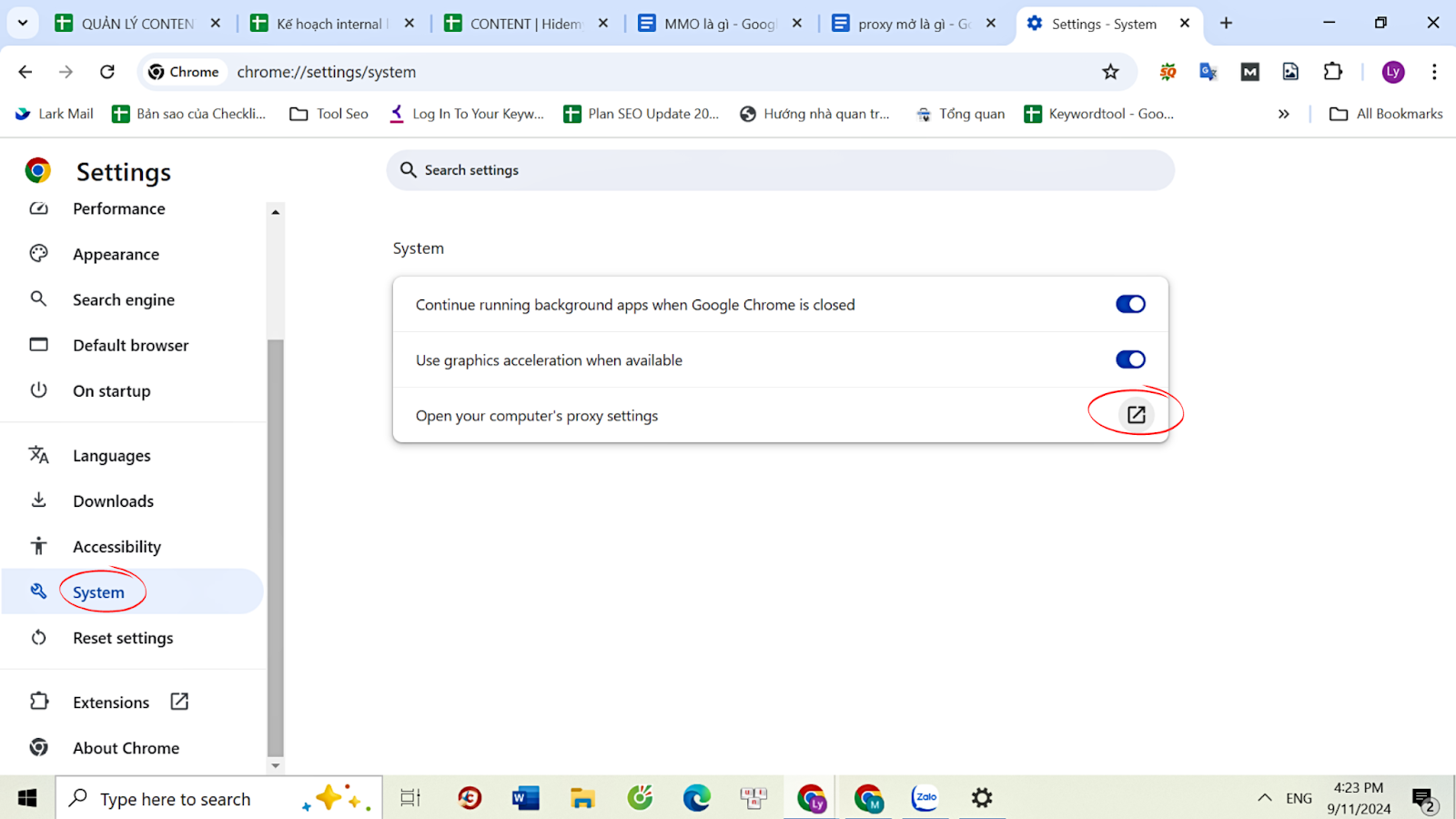
1 - On Windows:
-
Click the three dots in the top right corner of the browser.
-
Open the “Settings” tab.
-
Select “System,” then “Open your computer's proxy settings.”
-
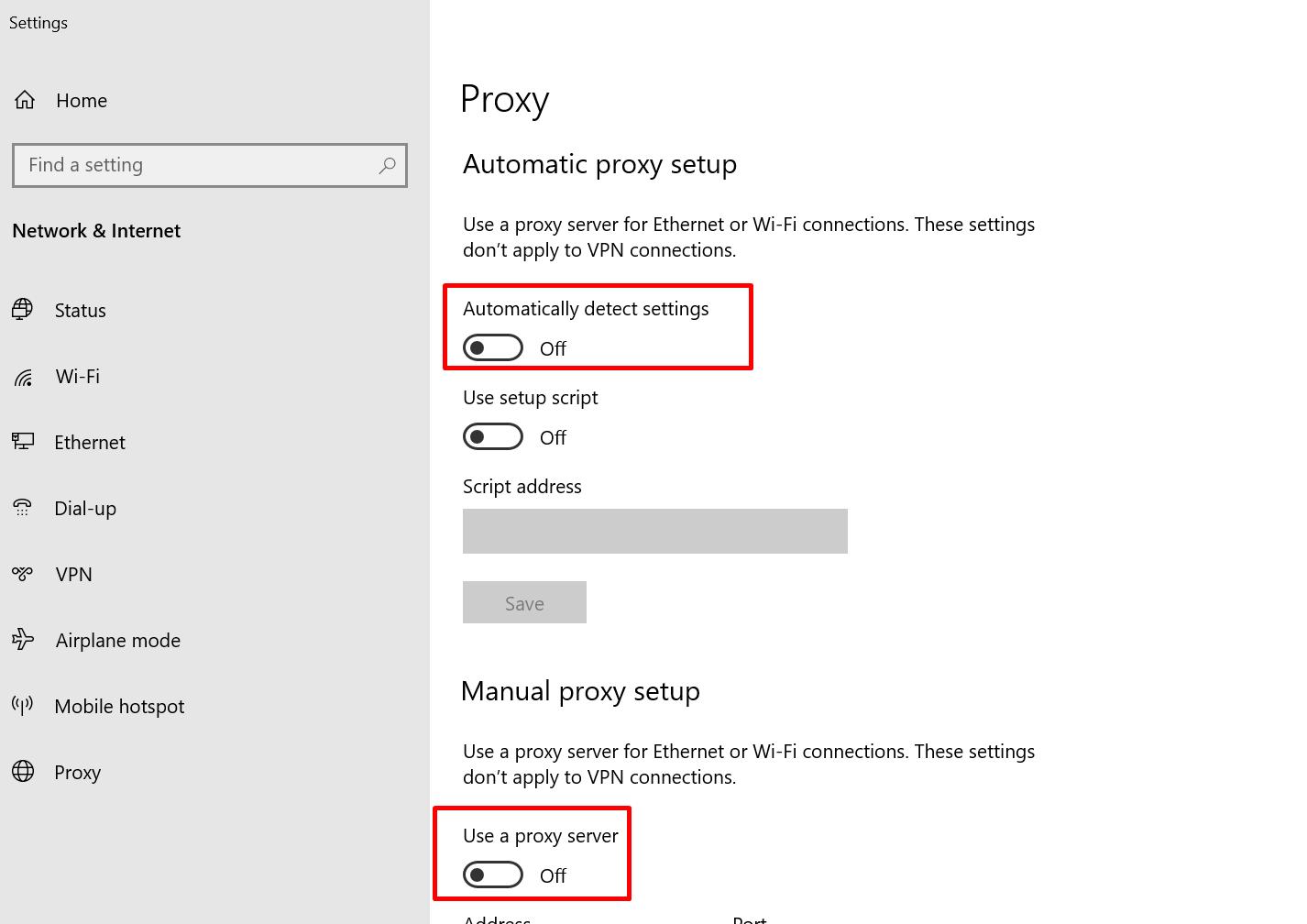
Under “Automatic proxy setup,” switch “Detect settings automatically” to Off.
-
Under “Manual proxy setup,” switch “Use proxy server” to Off.
-
Click “Save”.

2 - On Mac:
-
Select the three dots in the top right corner of the browser.
-
Select “Settings”.
-
Select “System”.
-
Click “Open your computer's proxy settings”.
-
Under the “Proxy” tab, uncheck all listed options.
-
Select “OK” to save the settings.
7. Should you use Open Proxy with Hidemyacc anti-detection browser?
The use of open proxies, such as HTML proxy or Socks proxy, can be done through the Hidemyacc anti-detection browser. This not only helps protect your identity, but also enhances your ability to manage multiple accounts on the same device without being detected.
Most people use proxies to avoid detection when accessing multiple accounts from the same IP address. Proxies help mask the original IP address, making tracking and detection more difficult. However, to manage multiple accounts effectively, simply changing IP is not enough. You'll also need to change your device's parameters, such as cookies, browser information, and other factors that websites can use to identify you.
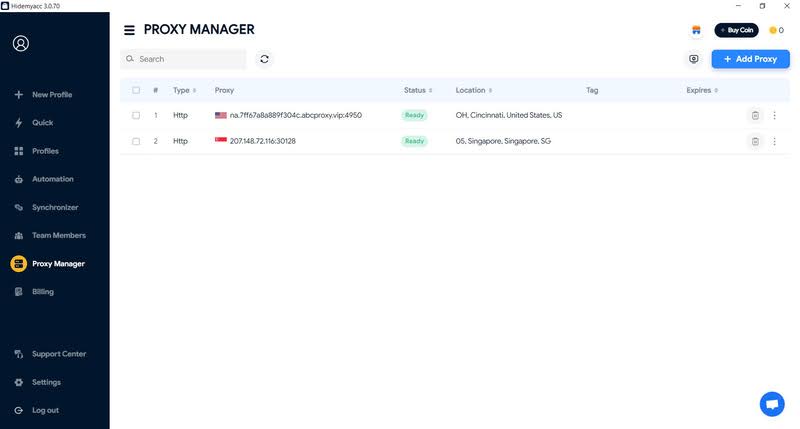
Benefits of using an open proxy via Hidemyacc:
-
Manage multiple accounts easily: Hidemyacc allows you to add proxies to each individual profile. This not only changes the IP address but also changes the browser parameters so that the website recognizes you as a new user. You can easily create and manage multiple accounts without the problem of duplicate IP addresses.
-
Increased security and anonymity: When connecting a proxy through Hidemyacc, you can better protect your identity. Antidetec Browser Hidemyacc provides tools to help anonymize and protect your personal information, preventing it from being tracked from websites and online services.
-
Easy configuration and connection: Hidemyacc supports proxy connection with just a few simple steps. You can add proxies for each profile and connect only once without having to reconfigure multiple times. This helps save time and effort during account management.
-
Avoid IP detection and bans: Using an open proxy via Hidemyacc helps minimize the risk of detection and IP ban when accessing multiple accounts from the same device. Hidemyacc ensures that your browser parameters and IP addresses are tightly managed, helping you maintain your online activities safely and efficiently.
Choosing the right open proxy can be a complicated task with the many options available. However, when combined with Hidemyacc anti-detection browser, you can take advantage of the outstanding benefits that open proxies bring.
Hopefully through the above article you have a better understanding What is an open proxy? as well as the advantages and disadvantages of this tool. With the support of Hidemyacc, connecting to an open proxy becomes simpler and more convenient than ever. You can try this feature with our free 7-day trial, which allows you to explore the full range of functions and benefits. Download Hidemyacc today and configure an open proxy to enhance your online experience with optimal anonymity and security.






